On Monday, U.S CISA added two security flaws to its Known Exploited Vulnerabilities Catalog. One of the discovered flaws is the recently revealed remote code execution bug that affects Zyxel firewalls.
The High-severity vulnerability tracked as CVE-2022-30525 has a CVE score of 9.8. It is related to a command injection flaw found in some select versions of the Zyxel firewall that could enable an authenticated adversary to execute arbitrary commands on the underlying operating system.
The device affected by the CVE-2022-30525 include:
- USG FLEX 100, 100W, 200, 500, 700
- USG20-VPN, USG20W-VPN
- ATP 100, 200, 500, 700, 800, and
- VPN series
In late April, the Taiwanese firm released a new firmware ZLD V5.30 to patch the above-mentioned vulnerability. Later on May 12, it was made publicly knowledgeable after a coordinated disclosure process with Rapid7.
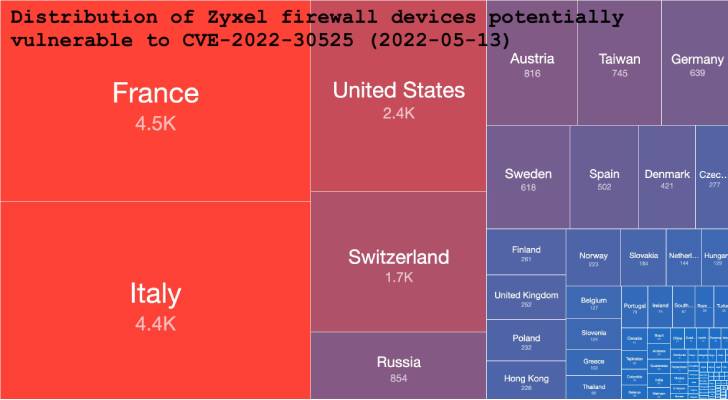
Just a day after the disclosure process, nonprofit security organization “Shadowserver Foundation” started detecting notorious attempts to exploit the vulnerability. Zyxel firewall devices within France, Italy, U.S, Switzerland, and Russia are more likely to be affected by the vulnerability.
Another vulnerability added by CISA to its catalog tracked as CVE-2022-22947 got a rating of 10 (highest) on the CVSS vulnerability scoring system.
The high severity vulnerability is another code injection vulnerability in Spring Cloud Gateway and can be exploited to enable arbitrary remote execution on a remote host via a tailor-made request. Later it was addressed in Spring Cloud Gateway versions 3.1.1 and newer or 3.0.7 or newer.
Are you looking for more security updates? Subscribe to our Newsletter for the latest security news updates.




