The FBI will soon start to share compromised passwords (Passwords leaked during data breach) with Have I Been Pwned’s ‘Password Pwned’ service that was identified while law enforcement investigations carried out.
The data breach notification website ‘Have I Been Pwned‘ incorporates a service listed as Pwned Passwords that allows the users to search for known compromised passwords and check whether your password has appeared in a data breach.
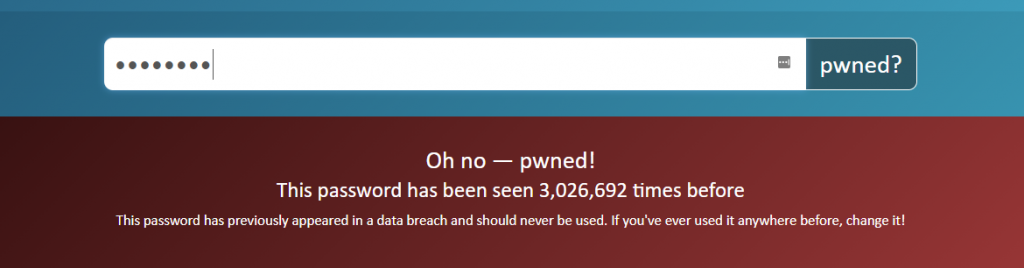
By using this service, a visitor can enter a password in input and recognize how many times that password has been exposed in a data breach. For instance, if we enter the password ‘12345678’, the service states that it has been seen 3,026,692 times in data breaches.
On Friday, Have I Been Pwned creator Troy Hunt announced that the FBI would be soon sharing the compromised passwords identified while the law enforcement investigations were being carried out into the Pwned Password service.
By sharing this feed, the FBI will let admins and users check for passwords that are known to be used for wicked and evil intents. Then, Admins will be able to modify or change the passwords before they are utilized in credential stuffing attacks and network breaches.
Bryan A. Vorndran, Assistant Director, Cyber Division, FBI said
We are thrilled to be partnering with HIBP on this significant project to protect victims of online credential theft. It is yet another example of how important public/private partnerships are in the fight against cybercrime.
HIBP:- Have I Been Pwned
The FBI will be sharing the passwords as SHA-1 and NTLM hash pairs that can then be searched utilizing the service or can be downloaded as part of Pwned Password’s offline list of passwords.
Password Pwned enables users to download the compromised passwords in the form of lists SHA-1 or NTLM hashed passwords which can be later utilized offline by Windows admins to check whether they are being utilized on the network or not.
Now, you will be able to download these lists with the hashes sorted alphabetically or by their prevalence. For instance, the list beneath displays the NTLM hash ’32ED87BDB5FDC5E9CBA88547376818D4′ being used over 24 million times.
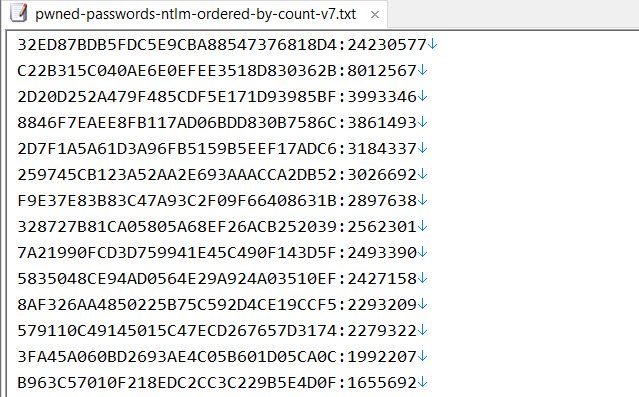
It is pretty much predictable that this NTLM hash is for the password ‘123456‘.
To help promote this new partnership, Hunt has made Password Pwned open source through the .NET Foundation and also is requesting other developers to help create a ‘Password Ingestion’ API.
The FBI and other law enforcement agencies can utilize this API to feed the compromised passwords into the Password Pwned database.
Looking for more Security News, subscribe to our newsletter and get regular updates on cybersecurity.




