According to new research by Eclypsium, about 300,000 MikroTik routers were found vulnerable to malware botnets.
For those who don’t know, MicroTik is a Lativian company that develops routers and wireless ISP systems and has sold more than 2M devices globally.
Out of these 2 million devices, about 300,000 devices were found to be vulnerable, as per a report published by Eclypsium on Thursday.
The security vulnerability was found in MikroTik’s devices mostly located in Brazil, Russia, China, Indonesia, and Italy.
The
Meanwhile, Eclypsium researchers scanned the Internet for MikroTik devices and found that at least 300,000 MikroTik devices are vulnerable to at least one of the following four CVEs:
- CVE-2019-3977: Remote OS downgrade and system reset. CVSS v3 – 7.5
- CVE-2019-3978: Remote unauthenticated cache poisoning. CVSS v3 – 7.5
- CVE-2018-14847: Remote unauthenticated arbitrary file access and write. CVSS v3 – 9.1
- CVE-2018-7445: Buffer overflow enabling remote access and code execution. CVSS v3 – 9.8
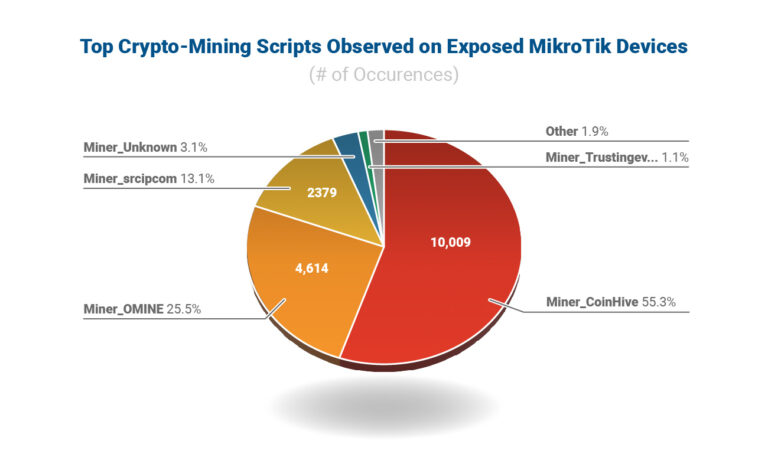
Additionally, the researchers found that the coin miners had infected about 20,000 of the devices and about half of them tried connecting to the now-offline CoinHive portal.
MikroTik has officially advised its clients to do the following necessary steps:
- Keep your MikroTik device up to date with regular upgrades.
- Do not open access to your device from the internet side to everyone. If you need remote access, only open a secure VPN service, like IPsec.
- Use a strong password, and even if you do, change it now!
- Don’t assume your local network can be trusted. Malware can attempt to connect to your router if you have a weak password or no password.
- Inspect your RouterOS configuration for unknown settings including: System -> Scheduler rules that execute a Fetch script. Remove these., IP -> Socks proxy. If you don’t use this feature or don’t know what it does, it must be disabled., L2TP client named “lvpn” or any L2TP client that you don’t recognize.
- Input firewall rule that allows access for port 5678.
- Block domains and tunnel endpoints associated with the Meris botnet.
Meanwhile, users can check their devices for vulnerability CVE-2018-14847 by using the MikroTik assessment tool released by Eclypsium.
Sign up for our newsletter to get the latest security news from various tech industries and cyber security firms.




