Several threat actors are now exploiting the bugs that were discovered in a type of server used to manage fleets of mobile devices. The malicious actors are exploiting the bugs to take control over crucial enterprise servers and even plan intrusions in the company networks.
MobileIron MDM servers are the targets of these attacks.
MDMS or Mobile Device Management Systems are used in enterprises to enable companies to manage the mobile devices of employees. System admins can deploy certificates, apps, access-control lists, and wipe stolen phones from a central server.
To carry out the features, MDM servers require to be online all the time and reach across the internet. Hence, remote employees’ phones can report back to the company and obtain the most current updates.
Table of Contents
Three Huge Vulnerabilities Identified in MobileIron MDMS
A few months back this summer, a security researcher named Orange Tsai identified three huge vulnerabilities in MobileIron’s MDM solutions that Tsai reported to the vendor. To which the company patched in July.
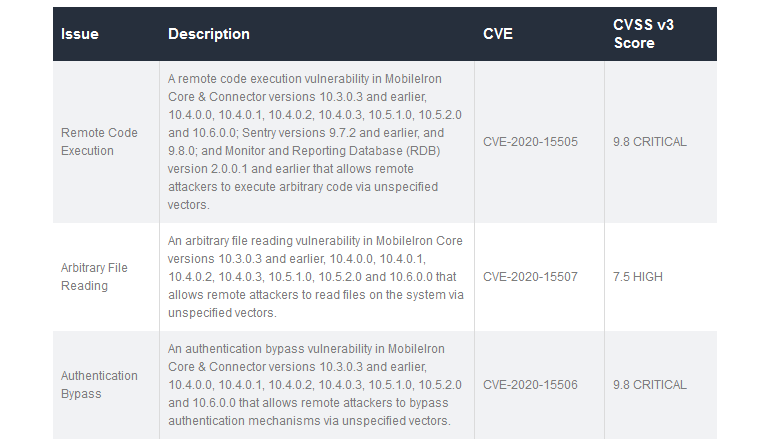
However, Tsai never released in-depth details of three bugs, this allowed companies to update their systems.
In September, Tsai gradually published a detailed write-up about the three bugs, after he applied one of the bugs to hack into Facebook’s MDM server and pivot to the organization’s internal network as part of Facebook’s bug bounty program.
Exploitation initiates after POC Published on GitHub
Though the Tsai’s blog post had some unintended consequences. Other security researchers utilized the details in the blog to build public proof-of-concept (POC) exploits for CVE-2020-15505.
This PoC exploit was later released on GitHub and made accessible to other security researchers and penetration testers, however, it was also exposed to attackers.
Are you looking for more security updates? Subscribe to our Newsletter for the latest security news right from the security and research industries. If you have any doubts, queries, or suggestions, please comment below in the comment box.




